eLearning professionals invest a lot of time and money in creating and using a learning management system (LMS) that can help others learn and grow. But did you know your LMS could be a potential target for hackers who can steal your data, disrupt your learning, or damage your reputation?
In this article, we will show you how insecure login mechanisms can pose a severe threat to your LMS. We will also guide you on how to overcome such threats with Tutor LMS, a secure and reliable WordPress LMS plugin that can protect your login credentials from cyberattacks.
Understanding the Risks of Insecure Logins
The consequences of an insecure login in LMS can be devastating if not handled appropriately, as it is one of the most common vulnerabilities. This article aims to analyze the widespread insecure login vulnerabilities in LMSs, the risk they pose to data, and the reputation of institutions. However, before diving into the details let’s first try to understand what an “insecure login” is.
Simply put, insecure login vulnerabilities are like gaps in the web application’s defense. This allows hackers to slip in and get hold of user login details. Some of the most frequent kinds of insecure login vulnerabilities are:
1. Weak Passwords
Weak passwords can be conveniently guessed or cracked through automated tools and wordlists. These passwords tend to be either too short or use well-known words or phrases, following an easily predictable pattern.
2. Password Reuse
This is when users use the same password for multiple accounts or websites. This increases the risk of compromise if one of the accounts or websites is breached and the password is exposed.
3. Phishing Attacks
These attacks trick users into entering their login credentials into malicious websites that look legitimate. For example, an attacker may send an email that appears to come from the LMS administrator, asking users to verify their account by clicking on a link that leads to a fake login page.
4. Brute Force Attacks
Brute force attacks involve notorious spammers who try to break into our private accounts by unleashing combination after combination of usernames and passwords. For instance, attackers may use a compilation of common usernames and passwords or experiment with different variations of a known password or username.
5. Social Engineering
These attacks manipulate users into revealing their login credentials and other sensitive information. An attacker may call or email a user pretending to be someone they trust, such as a colleague, a friend, or a support agent, and ask them for their password or other details.
The High Stakes of Insecure Login: Consequences for Your LMS and Users
Insecure login vulnerabilities can have serious consequences for your LMS and your users. Some of the potential consequences are:
- Data Breaches: Compromising the integrity and confidentiality of your data and exposing you to legal liabilities.
- Identity Theft: Impersonating your users and accessing their personal information.
- Financial Loss: Disrupting your operations, demanding ransom, or stealing your funds.
- Reputational Damage: Exposing your data breach publicly, defacing your website, or sending malicious messages to your users.
Addressing the Challenges of Secure Login With Tutor LMS
Keeping your online learning platform secure is paramount, and Tutor LMS recognizes this responsibility. In an era where online threats are rampant, Tutor has taken multiple measures to protect users from fraud and spam. To achieve this, Tutor LMS has introduced four novel builtin settings:
- Two-Factor Authentication
- Fraud Protection
- Email Verification
- Social Login
Let’s explore how the “Authentication” tab can help you secure your Tutor LMS platform with different security features. The Authentication tab lets you turn on or off various options that can help you safeguard your learners’ data and keep out intruders. To begin, go to Tutor LMS Pro > Settings > Authentication tab.
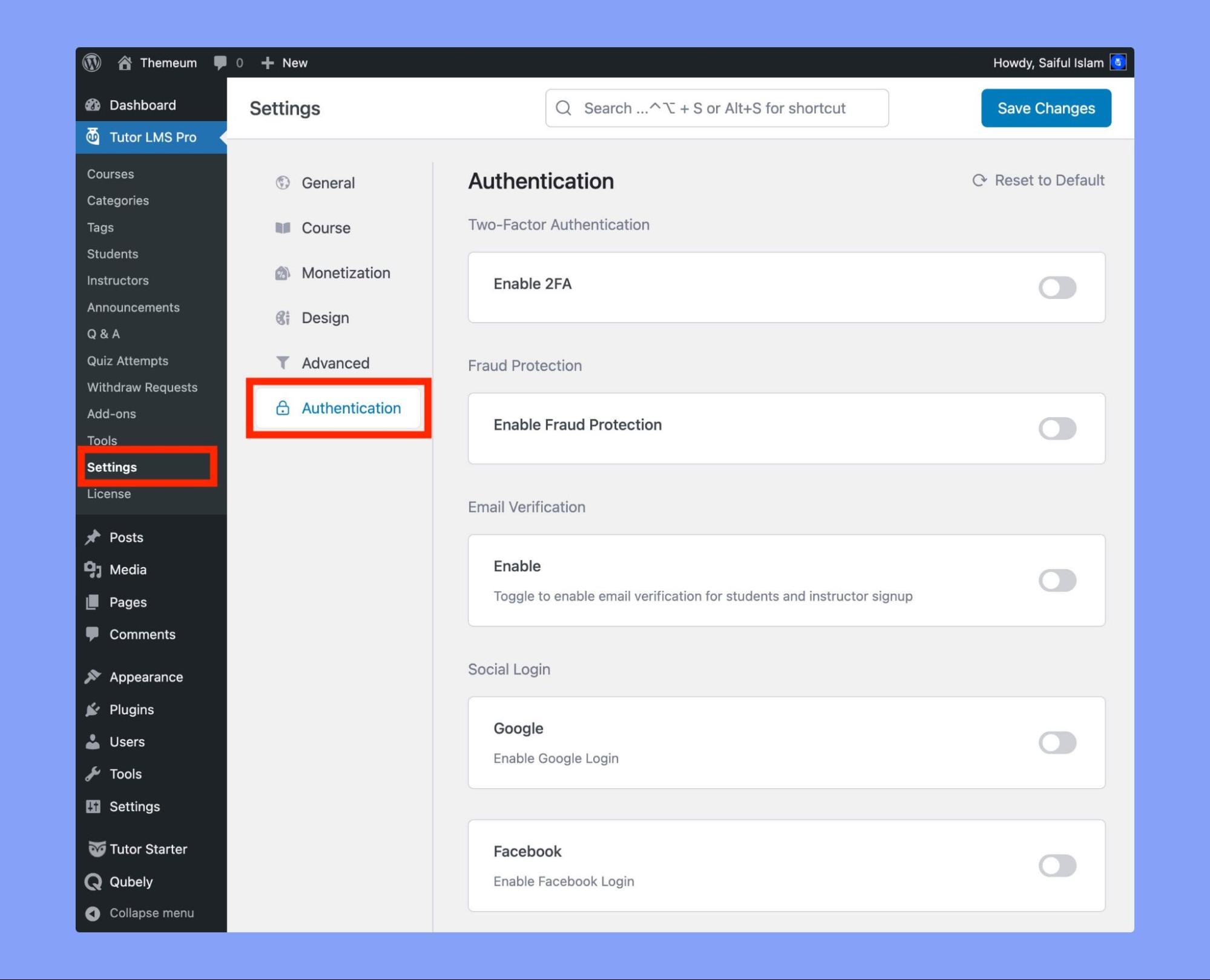
Tutor provides a high level of assurance for the safety and security of users’ login credentials. As mentioned above Tutor LMS Pro incorporates several practical login security features. Let’s examine these features in detail:
Two-Factor Authentication (2FA)
Tutor LMS incorporates a formidable two-factor authentication (2FA) measure to enhance its login security. This feature requires users to enter a unique code, in addition to their login credentials.
With 2FA enabled users will receive a verification email containing a six-digit OTP (one-time password) and a verification link. This makes it extremely difficult for unauthorized users to “Brute Force Attack” and gain access to your LMS site.
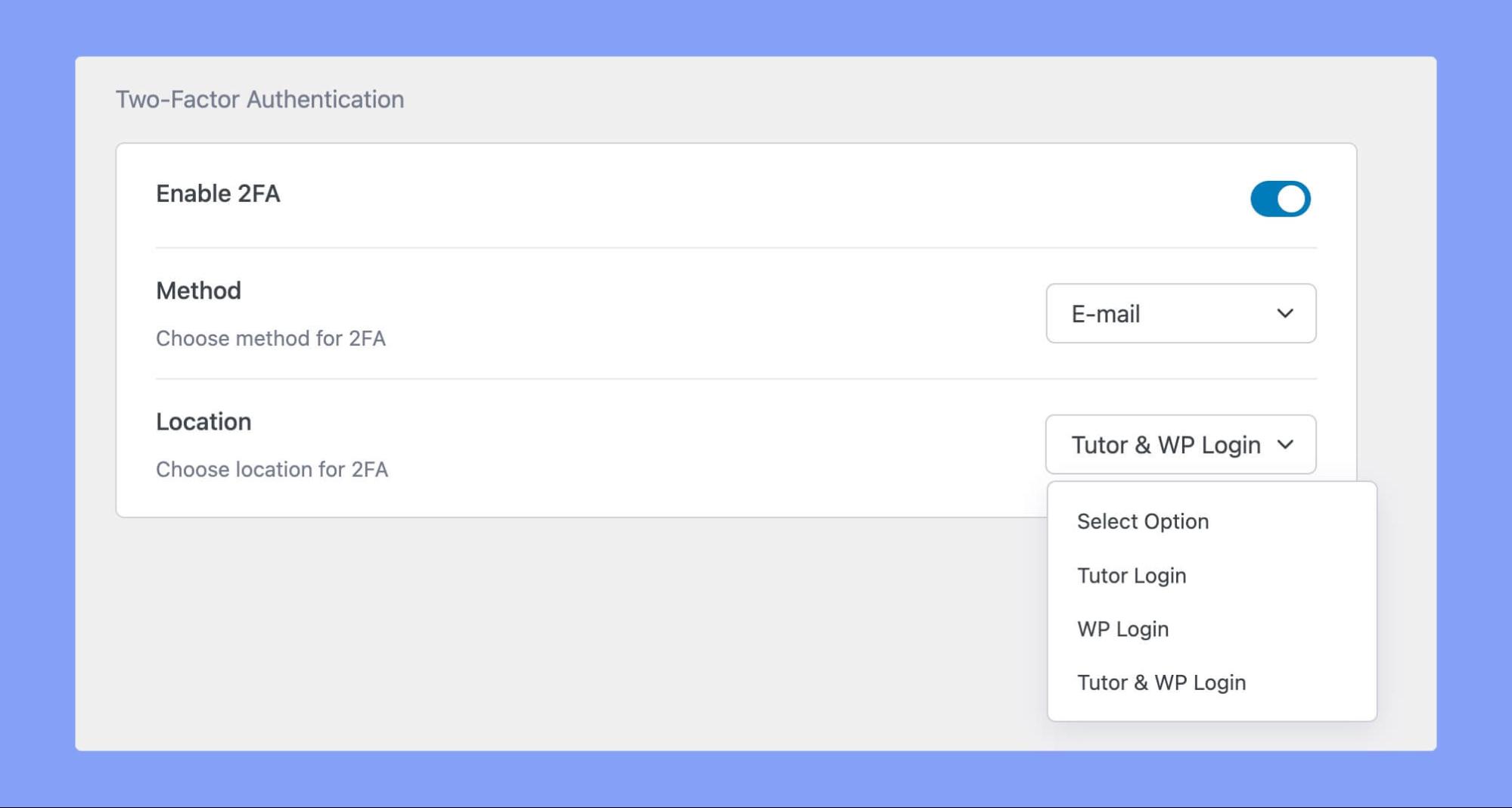
Setting up the 2FA method in Tutor LMS is very simple. From the Authentication tab in Tutor LMS settings, simply enable the “Two-Factor Authentication” method. Then select the location where you want to add this feature from the dropdown menu titled “Locations”. You have the option to add 2FA verification to the Tutor Login page, the WordPress Login, or both!
And if you don’t receive the OTP or if it expires, don’t worry! You can always request another OTP after just one minute.
Tip: You need to set up the SMTP server properly to send the Email OTP. To learn more on this visit our detailed guide here.
Fraud Protection
Tutor LMS login security includes a fraud protection feature that uses machine learning to detect and block suspicious login attempts. This feature can help prevent users from falling prey to “Phishing Attacks” that lead them to enter their login credentials into a fake website.
With Tutor LMS, you can easily activate the Fraud Protection feature to prevent such activities. You have two options to choose from when setting it up HoneyPot or Google reCAPTCHA.
HoneyPot creates a hidden text input field to trick bots, while Google reCAPTCHA requires users to complete image recognition challenges or click a checkbox. We recommend using
Google reCAPTCHA v3, as it’s the latest and most advanced method that offers fraud protection under the hood without annoying image recognition challenges.
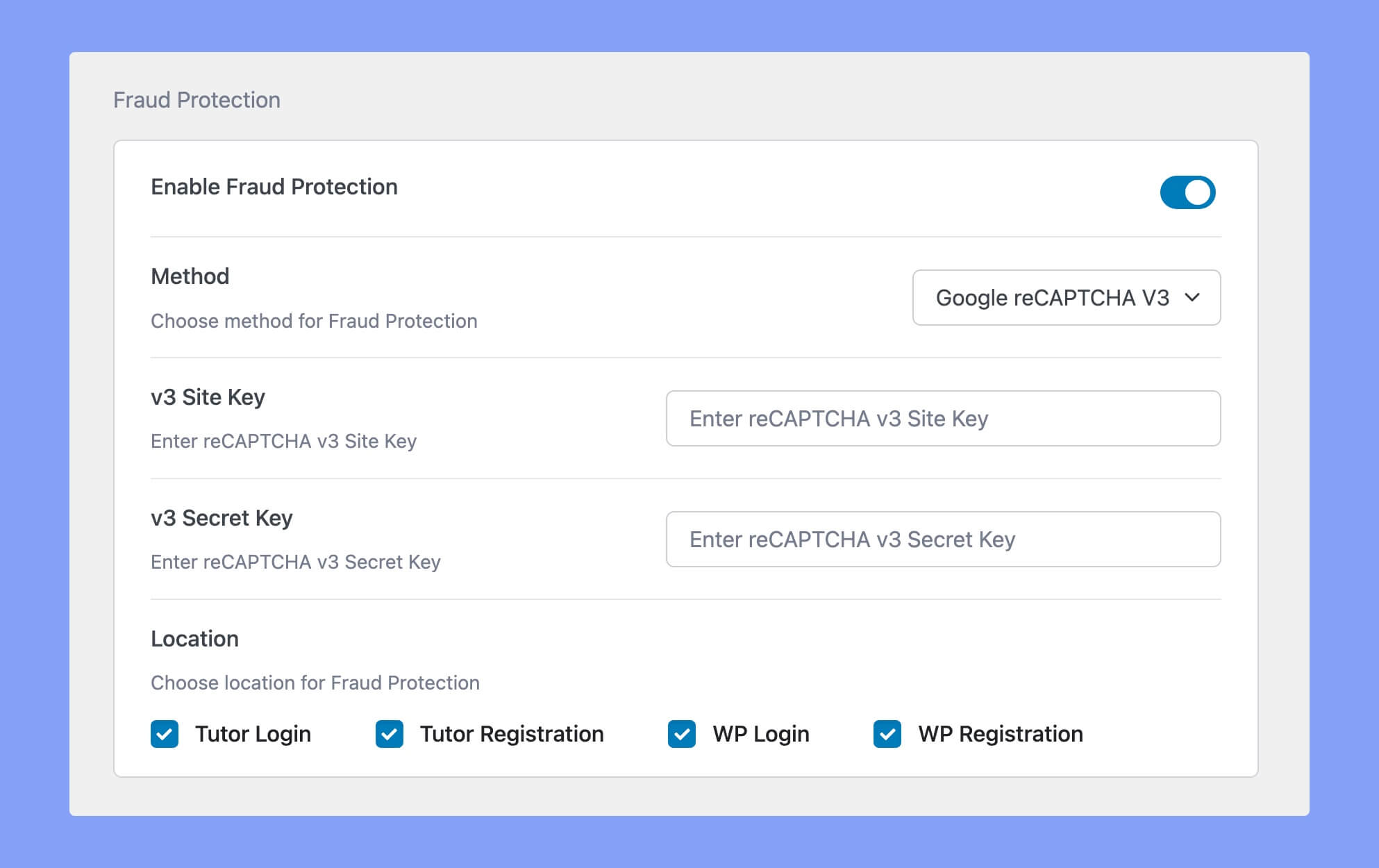
Setting up Fraud Protection is also very simple. Just navigate to the “Authentication” tab and enter the corresponding Site and Secret keys for your chosen method. You can set up this protection for Tutor Login, Tutor Registration, WP Login & WP Registration pages. Keep your platform safe and secure with Tutor LMS’s Fraud Protection!
Email Verification
Another important security feature is Email Verification, which requires users to verify their email address before they can access the platform. This makes it harder for attackers to create fake accounts and use “Social Engineering Tactics” to manipulate users into revealing sensitive information.
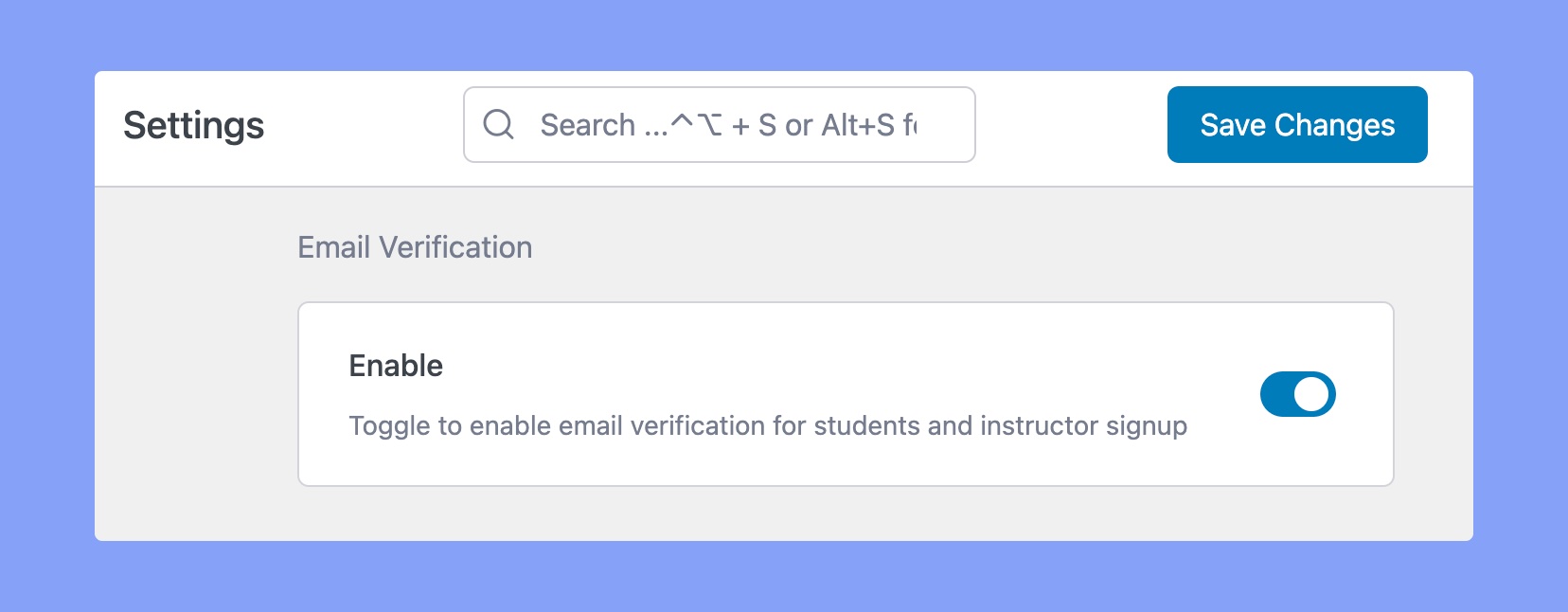
This safeguard acts as an extra layer of security to both student’s and teacher’s sign-up process by requiring email verification. When enabled, users will receive an automated email with a verification link that they must click before accessing the platform for the first time.
To activate this feature, all you need to do is navigate to the Authentication tab in the Tutor LMS Pro settings and toggle the “Email Verification” option. It’s that simple!
Social Login
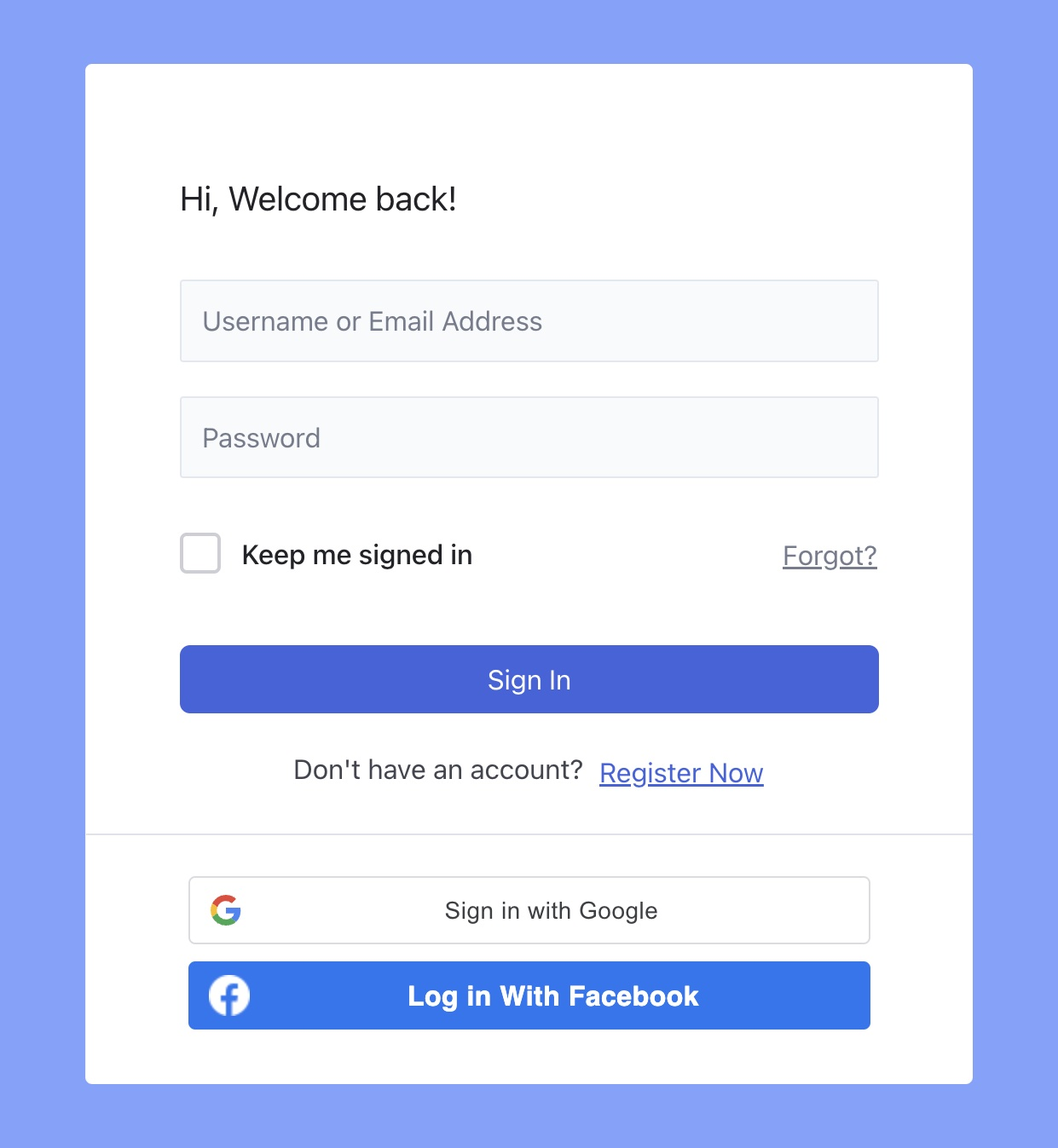
Want to make it easier for your students to log in to your Tutor LMS platform? Enable the Social Login option! With this feature, your students can quickly and easily use their Facebook or Google accounts to log in.
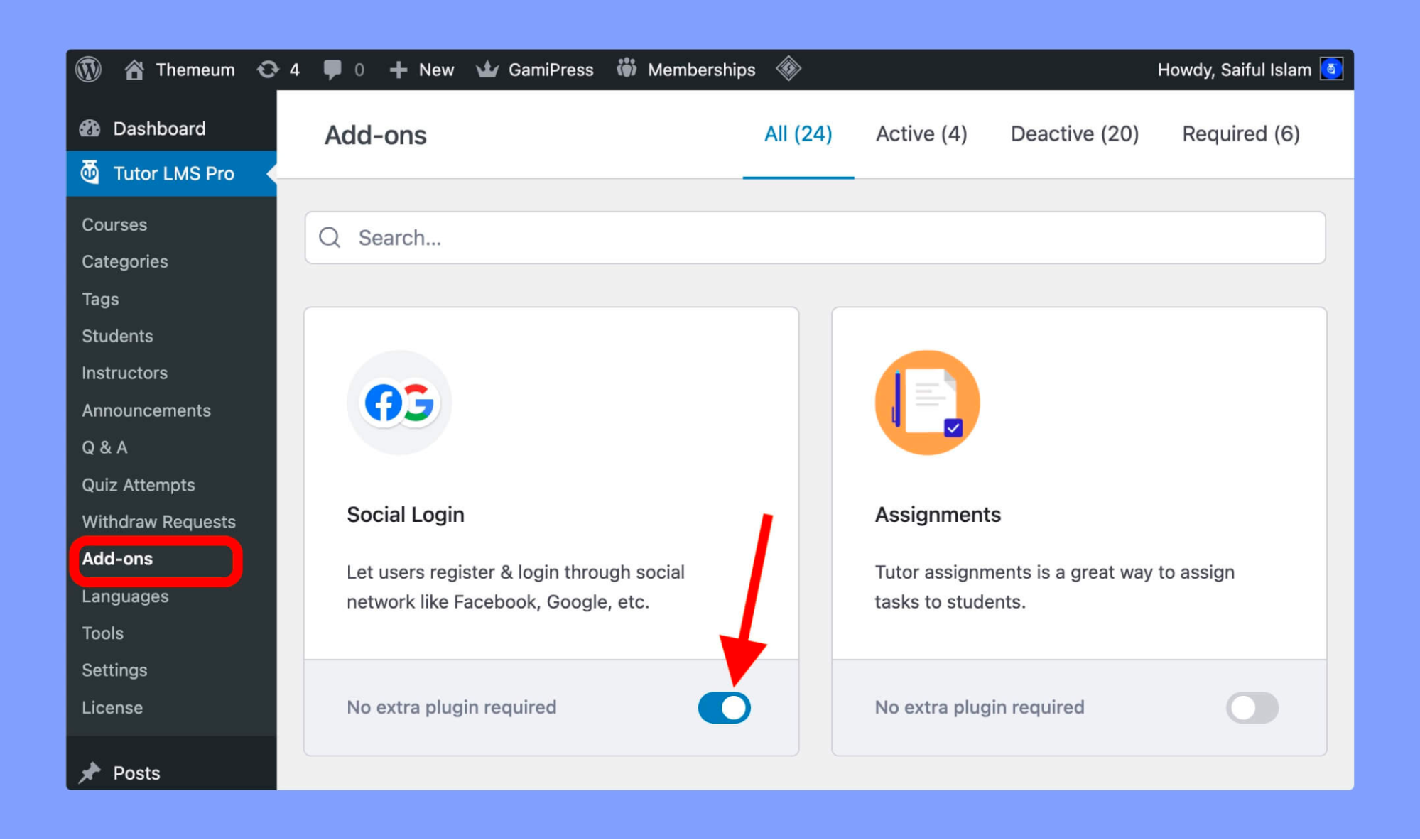
Just make sure to enable the Social Login add-on in Tutor LMS Pro > Add-ons. Once enabled, you can integrate both Facebook and Google login functionality. To do so navigate to Tutor LMS Pro > Settings > Authentication tab and scroll down to the Social Login section. Here you can enable the Google and Facebook login methods by clicking the toggle button.
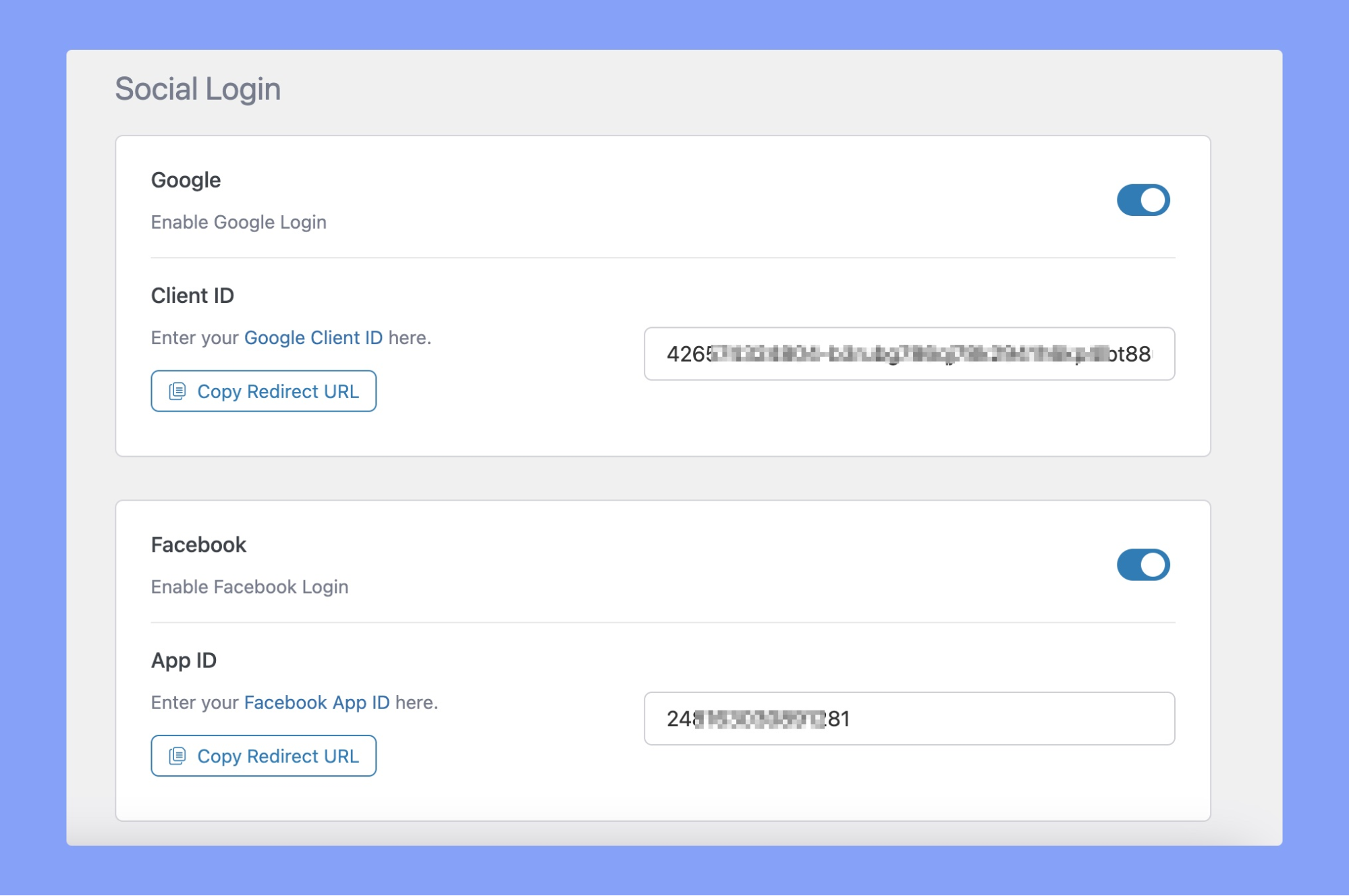
Our detailed guide on accessing your Facebook and Google API is now available. This guide provides step-by-step instructions on obtaining and using your API key for various purposes.
Enabling this feature reduces the user’s likelihood of reusing passwords across multiple accounts. More so, you make it easier for your users to sign up and log in and increase the chances of getting more signups as the registration process becomes quicker and more convenient.
Best Practices for Secure Login in Learning Management Systems
Ensuring a secure login process is vital for safeguarding user accounts and maintaining the integrity of learning management systems. While Tutor LMS implements robust security measures, it’s essential to reinforce protection through additional best practices. This section will outline effective strategies to enhance login security in learning management systems. Here are some key recommendations:
- Educate Users: Raise awareness among your users about security risks and best practices. Educate them on creating strong passwords, utilizing two-factor authentication, identifying and avoiding phishing emails, keeping software up to date, and promptly reporting suspicious activities.
- Update Software: Regularly update your WordPress core, plugins, themes, and server software. Staying current with security patches and bug fixes helps prevent potential vulnerabilities that hackers may exploit.
- Backup Data: Implement regular backups of your system’s data and store it securely. In the event of a disaster or data loss, having reliable backups ensures that you can restore your site promptly.
- Employ a Firewall: Utilize a firewall either on your server or via a reputable third-party service. Firewalls act as a protective barrier, filtering out malicious traffic and thwarting potential attacks before they reach your site.
- Conduct Site Audits: Conduct periodic security and performance audits using dedicated tools or services. These audits scan your site for malware, vulnerabilities, errors, and other issues, allowing you to identify and address any potential threats or functional problems.
Implementing these best practices can fortify your learning management system’s login security and establish a robust defense against unauthorized access and malicious activities. Remember, proactive measures and user education are essential in maintaining a safe online learning environment. Furthermore, for a comprehensive understanding of the top WordPress security practices, we offer an exclusive article.
Last Words
Okay, let’s wrap this up! We’ve covered a lot about LMS security, from password best practices to the importance of staying updated. It might seem a bit overwhelming, but truly, taking these steps to protect your eLearning platform is worth it. Think of it this way: a secure LMS builds trust with your learners. They know their information is safe, and that lets them focus on what matters – learning and growing.
And remember, you don’t have to navigate this alone. Tutor LMS, one of the best WordPress plugins for secure online learning, offers robust built-in security features to help you safeguard your platform. Plus, with regular updates and a commitment to user safety, you can feel confident that your eLearning environment is in good hands.
Start Using Tutor LMS Today
Ready to take your online courses to new heights? Download Tutor LMS now and enjoy a journey of eLearning excellence.
